Certificate Management System comes with various policy plug-in modules that help you govern its certificate generation and management operations.
The modules provided out of the box can be categorized into two groups:
Note that Certificate Management System doesn't come with key archival and recovery policy modules.
Constraints-Specific Policy Plug-in Modules
Constraints-specific policy plug-in modules help you define rules or constraints that Certificate Management System must use to evaluate an incoming request. Table 15.3 lists the constraints-specific policy plug-in modules provided out of the box. You can use these modules, as applicable, for defining the required policy rules for your Certificate Manager or Registration Manager; no plug-ins are provided for the Data Recovery Manager.
Default Revocation Policy
The default revocation policy applies to end-entity certificate revocation. The policy enforces a rule that only currently valid certificates can be revoked; an expired certificate cannot be revoked. The policy also looks at the revocation reason specified in the revocation form and sets the appropriate CRLReason extension.
Plug-in for Default Revocation Policy
The plug-in module provided for the default revocation policy is identified as follows:
com.netscape.certsrv.policy.DefaultRevocation
Configurable Parameters
Figure 15.1 shows how the configurable parameters pertaining to the DefaultRevocation policy plug-in implementation are displayed in the CMS window.
Figure 15.1 Parameters and values for the DefaultRevocation module
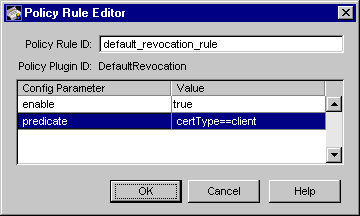
The configuration shown in Figure 15.1 enforces a rule that only valid client
certificates can be revoked; expired certificates cannot be revoked.
Table 15.4 gives details about each of these parameters.
DSA Key Constraints Policy
The DSA key constraints policy applies to end-entity certificate enrollment and renewal requests. The policy imposes constraints on the following:
The policy restricts the key size to one of the sizes, such as 512, 1024, or 2048, supported by the Certificate Management System. In other words, this policy allows you to set up restrictions on the lengths of public keys certified by Certificate Management System. For example, you can configure a Certificate Manager to certify public keys up to 1024 bits in length for end users.
Plug-in for DSA Key Constraints Policy
The plug-in module provided for the DSA key constraints policy is identified as follows:
com.netscape.certsrv.policy.DSAKeyConstraints
Configurable Parameters
Figure 15.2 shows how the configurable parameters pertaining to the DSAKeyConstraints policy plug-in implementation are displayed in the CMS window.
Figure 15.2 Parameters and values for the DSAKeyConstraints module
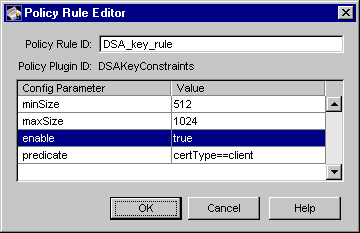
The configuration shown in Figure 15.2 restricts the minimum and maximum key sizes for all client certificates to 512 and 1024, respectively.
Table 15.5 gives details about each of these parameters.
Key Algorithm Constraints Policy
The key algorithm constraints policy applies to end-entity certificate enrollment and renewal requests. The policy restricts the key algorithm requested to one of the algorithms, such as RSA or DSA, supported by Certificate Management System. In other words, this policy allows you to set restrictions on the types of public keys certified by Certificate Management System.
For example, you can configure a Certificate Manager to certify only those public keys that comply with the PKCS-1 RSA Encryption Standard.
Plug-in for Key Algorithm Constraints Policy
The plug-in module provided for the key algorithm constraints policy is identified as follows:
com.netscape.certsrv.policy.KeyAlgorithmConstraints
Configurable Parameters
Figure 15.3 shows how the configurable parameters pertaining to the KeyAlgorithmConstraints policy plug-in implementation are displayed in the CMS window.
Figure 15.3 Parameters and values for the KeyAlgorithmConstraints module
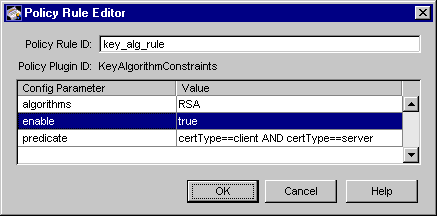
The configuration shown in Figure 15.3 restricts the key algorithm of all client and server certificates to RSA.
Table 15.6 gives details about each of these parameters.
Renewal Validity Constraints Policy
The renewal validity constraints policy applies to end-entity certificate renewals. It governs the formulation of content in the renewed certificate based on the currently issued certificate. The policy enforces the following rules:
The renewal process to which this policy is applied can be manual (request needs to be approved by an agent) or automated; for details, see "Certificate Renewal". In both cases, the currently issued certificate must be either presented during SSL client authentication by the end entity or selected by the agent approving the renewal request.
You should consider using this policy if you want to enforce the following:
Plug-in for Renewal Validity Constraints Policy
The plug-in module provided for the renewal validity constraints policy is identified as follows:
com.netscape.certsrv.policy.RenewalValidityConstraints
Configurable Parameters
Figure 15.4 shows how the configurable parameters pertaining to the RenewalValityConstraints policy plug-in implementation are displayed in the CMS window.
Figure 15.4 Parameters and values for the RenewalValidityConstraints module
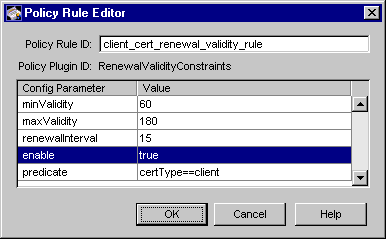
The configuration shown in Figure 15.4 enforces a rule that only those client
certificates that are due to expire within the next 15 days can be renewed. The
renewed certificates are valid for at least 60 days (two months) and require
renewing after 180 days (six months).
Table 15.7 gives details about each of these parameters.
RSA Key Constraints Policy
The RSA key constraints policy applies to end-entity certificate enrollment and renewal requests. The policy imposes constraints on the following:
The policy restricts the key size to one of the sizes, such as 512, 1024, or 2048, supported by Certificate Management System. In other words, this policy allows you to set restrictions on the length of public keys certified by the Certificate Management System.
For example, you can configure a Certificate Manager to certify public keys up to 1024 bits in length for end users.
Plug-in for RSA Key Constraints Policy
The plug-in module provided for the RSA key constraints policy is identified as follows:
com.netscape.certsrv.policy.RSAKeyConstraints
Configurable Parameters
Figure 15.5 shows how the configurable parameters pertaining to the RSAKeyConstraints policy plug-in implementation are displayed in the CMS window.
Figure 15.5 Parameters and values for the RSAKeyConstraints module
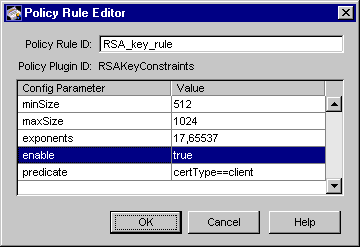
The configuration shown in Figure 15.5 restricts the minimum and maximum key sizes for all client certificates to 512 and 1024, respectively.
Table 15.8 gives details about each of these parameters.
Validity Constraints Policy
The validity constraints policy applies to end-entity certificate enrollment requests. The policy enforces minimum and maximum validity periods for certificates and changes them if the policy is not met. Specifically, the policy imposes constraints on the following:
If this policy rule is enabled, the server applies the rule to the certificate request being processed, and then determines if the validity period in the request is acceptable. The rule checks two X.509 attributes of the certificate, the notBefore and notAfter time, which together indicate the total validity life of a certificate, to make sure that they conform to the configured ranges.
The rule checks that the value of the notBefore attribute in the request is not more than leadTime minutes in the future; the leadTime is a configurable parameter in the plug-in implementation. The ability to configure the value of the leadTime parameter in the policy rule allows you to prohibit end entities from requesting certificates whose validity starts too far in the future, and yet allows some amount of toleration of clock-skew problems. For example, if the current date and time is 01/15/1999 (mm/dd/YYYY) and 1:30 p.m., the value of the notBefore attribute is set to 3:00 p.m., and that the leadTime is 10 minutes, then the request would fail, because the validity requested begins more than 10 minutes in the future.
The rule also checks that the value of the notBefore attribute in the request is not more than lagTime minutes in the past. For example, if the current date and time is 01/15/1999 (mm/dd/yyyy) and 1:30 p.m., the value of the notBefore attribute is set to 1:15p.m., and the lagTime is set to 10 minutes, the request would fail because the user has requested a certificate 15 minutes in the past. Note that a request with notBefore set to 1:25 p.m. would have passed, however.
Note
Currently, CRMF is the only enrollment format which allows an end entity to
request a specific validity period.
It can be useful to restrict the length of the validity period for certificates issued by Certificate Management System. For example, if you want users to renew their certificates at least once a year, you can set the maximum validity period to one year. If you want to limit the frequency of certificate renewals to keep down administrative costs, you can set the minimum validity period to six months.
Plug-in for Validity Constraints Policy
The plug-in module provided for the validity constraints policy is identified as follows:
com.netscape.certsrv.policy.ValidityConstraints
Configurable Parameters
Figure 15.6 shows how configurable parameters pertaining to the ValidityConstraints policy plug-in implementation are displayed in the CMS window.
Figure 15.6 Parameters and values for the ValidityConstraints module
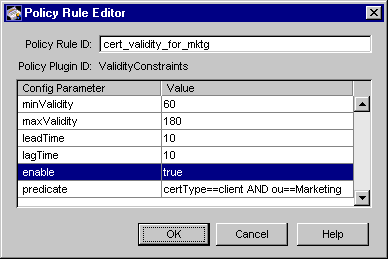
The configuration shown in Figure 15.6 enforces a rule that all client certificates requested by end entities in an organizational unit (OU) called Marketing are valid for at least 60 days (two months) and require renewing after 180 days (six months).
Table 15.9 gives details about each of these parameters.
Extension-Specific Policy Plug-in Modules
Since its initial publication, the X.509 standard for certificate formats has been amended to include additional information within a certificate. Version 3, the latest version, allows you to add additional information as certificate extensions. For example, Netscape applications (Netscape Navigator 3.0 or higher, and Enterprise Server 2.01 or higher) support an extension that specifies the type of certificate issued (such as client, server, or object signing).
Extension-specific policy plug-in modules help you configure Certificate Management System to set specific extensions on certificates it issues. When deciding whether to enable or disable any of the X.509 v3 certificate extensions, keep in mind that not all applications support X.509 v3 extensions. Among the applications that do support extensions, not all applications will recognize a given extension. For general guidelines on using extensions in certificates, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Table 15.10 lists extension-specific policy plug-in modules supported out of the box. You can use these modules to define the policy rules for your Certificate Manager and Registration Manager.
Authority Key Identifier Extension Policy
The authority key identifier extension policy plug-in implementation is based on the Authority Key Identifier extension. This extension identifies the public key that corresponds to the private key used by a CA to sign certificates.
The key identifier set in the extension is the MD5 hash of the issuer's public key.
If enabled, this policy adds the authority key identifier extension to all certificates issued, unless the predicate specifies otherwise. You should consider using this extension for all CA certificates (root as well as subordinate) issued by Certificate Management System, especially when a Certificate Manager has multiple signing keys (either due to multiple concurrent key pairs or due to changeover).
For general guidelines on setting the authority key identifier extension, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Plug-in for Authority Key Identifier Extension Policy
The plug-in module provided for the authority key identifier extension policy is identified as follows:
com.netscape.certsrv.policy.AuthorityKeyIdExt
Configurable Parameters
Figure 15.7 shows how the configurable parameters pertaining to the AuthKeyIDExt policy plug-in implementation are displayed in the CMS window.
Figure 15.7 Parameters and values for the AuthorityKeyIdentifierExt module
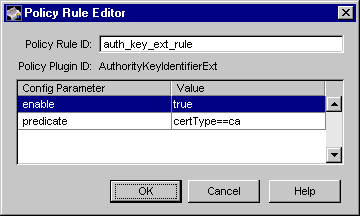
The configuration shown in Figure 15.7 enforces a rule that the authority key identifier extension must be set in all CA certificates.
Table 15.11 gives details about each of these parameters.
Basic Constraints Extension Policy
The basic constraints extension policy plug-in implementation is based on the Basic Constraints extension defined in X.509 and PKIX standard rfc 2459 (see http://www.ietf.org/rfc/rfc2459.txt). This extension identifies whether the Certificate Manager is a CA. In addition, the extension is also used during the certificate chain verification process to identify CA certificates and to apply certificate chain-path length constraints.
Note
The current PKIX standard requires that this extension be marked critical and
that it appear in all CA certificates. The standard also recommends that the
extension should not appear in end-entity certificates.
If enabled, this policy adds the basic constraints extension to all certificates being issued, unless specified otherwise by the predicate expression. To add the extension to subordinate CA certificates only, you must configure the predicate expression to be certType==ca.
For general guidelines on setting the basic constraints extension, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Plug-in for Basic Constraints Extension Policy
The plug-in module provided for the basic constraints extension policy is identified as follows:
com.netscape.certsrv.policy.BasicConstraintsExt
Configurable Parameters
Figure 15.8 shows how the configurable parameters pertaining to the BasicConstraintsExt policy plug-in implementation are displayed in the CMS window.
Figure 15.8 Parameters and values for the BasicConstraintsExt module
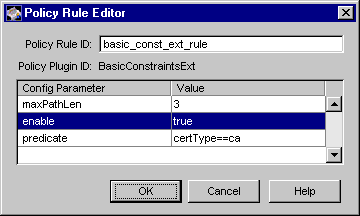
The configuration shown in Figure 15.8 enforces a rule that the basic constraints extension must be set in all CA certificates.
Table 15.12 gives details about each of these parameters.
CRL Distribution Point Extension Policy
The CRL distribution point extension policy plug-in implementation is based on the CRL Distribution Point extension. If enabled, this policy inserts a CRLDistributionPoint extension into each certificate being issued, unless the predicate expression specifies otherwise. Essentially, the extension identifies one or more CRL distribution points or locations where the CRL for the certificate (that includes the extension) can be obtained. For information on configuring a Certificate Manager to publish CRLs to different distribution points, see "CRL Issuing Points".
Certificate Management System supports only two name forms for distribution points out of the box: X.500 Directory Name and URI. URIs described in this document support two CRL retrieval mechanisms: LDAP-based and HTTP-based.
Optionally, each distribution point may contain a set of reason flags, indicating what revocation reasons are covered by the CRL at that location. Also, the distribution point location can be relative to the location of the issuer. In this last case, the issuerName and issuerType parameters should be included to give the location of the issuer.
Note that you can configure the server to support any name form by changing the sample code provided for this purpose. You can find the code in a directory named SDK on the product CD. You can also download the samples from this site:
http://home.netscape.com/eng/server/cms
For general guidelines on setting the CRL distribution point extension in certificates, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Plug-in for CRL Distribution Point Extension Policy
The plug-in module provided for the CRL distribution point extension policy is identified as follows:
com.netscape.certsrv.policy.CRLDistributionPointsExt
Configurable Parameters
Table 15.13 gives details about each of the configurable parameters pertaining to the CRLDistributionPointsExt policy plug-in implementation.
Adding Distribution Points to the Configuration File
If you configure the CRL distribution point policy to contain more than two distribution points, you should add the configuration parameters pertaining to the remaining distribution points to the configuration file. The parameters you're required to add include the following:
where, <subsystem> must be the prefix designated to the CMS subsystems--it is ca for the Certificate Manager and ra for the Registration Manager--to which the rule belongs.
To add CRL distribution point-specific parameters to the server's configuration:
Stop the CMS instance; see "Stopping Certificate Management System".
Open the configuration file in a text editor; to locate the file, see "Locating the Configuration File".
Add the configuration parameters to the file; see the configuration sample at the end of this procedure.
Save your changes, and close the configuration file.
Start the CMS instance; see "Starting Certificate Management System".
The sample parameters shown below indicate how to create a CRL distribution point extension policy rule for a Certificate Manager. In the sample, note the following:
Key Usage Extension Policy
The key usage extension policy plug-in implementation is based on the Key Usage extension. This extension specifies for what purposes the key contained in the certificate should be used: whether the key should be used for data signing, key encipherment, or data encipherment. You can use this extension to restrict the usage of a key pair (or certificate). For example, you can restrict a certificate to be used for digital signature only.
If enabled, the policy adds the key usage extension to all certificates being issued, unless the predicate expression specifies otherwise. The bits set in the key usage extension are formed from the following HTTP input variables:
The input variables are embedded as hidden values in the default enrollment forms--the directory-based enrollment form (DirUserEnroll.html), directory- and PIN-based enrollment form (DirPinUserEnroll.html), and manual enrollment form (ManUserEnroll.html). For details about these forms, see "Forms for Certificate Enrollment".
Figure 15.9 shows the default directory-based enrollment form for end users with the information related to the key usage extension variables highlighted--it shows three of the total number of variables listed above, digital_signature, non_repudiation, and key_encipherment, indicating that these bits be set in certificates requested using this form.
Figure 15.9 Key usage extension-specific variables in enrollment forms
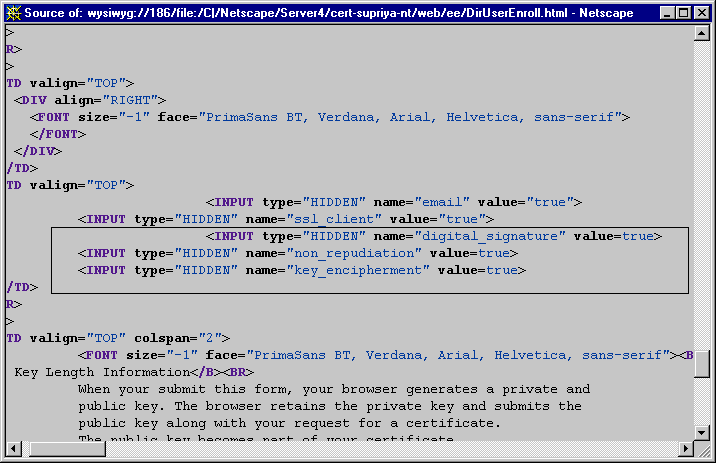
Note that by default only a few variables are included in the form and all their values are set to true. You should make the appropriate modifications to suit your requirements. When adding new variables, the HTML input format must be as follows:
<input type="HIDDEN" name="variable_name" value=true>
where, variable_name can be any of the HTTP input variables mentioned above.
For general guidelines on setting the key usage extension, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Plug-in for Key Usage Extension Policy
The plug-in module provided for the key usage extension policy is identified as follows:
com.netscape.certsrv.policy.KeyUsageExt
Configurable Parameters
Figure 15.10 shows how the configurable parameters pertaining to the KeyUsageExt policy plug-in implementation are displayed in the CMS window.
Figure 15.10 Parameters and values for the KeyUsageExt module
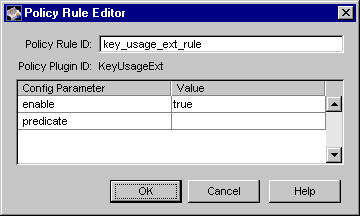
The configuration shown in Figure 15.10 enforces a rule that the key usage extension must be set in all certificates.
Table 15.14 gives details about each of these parameters.
Netscape Certificate Type Extension Policy
The Netscape certificate type extension policy plug-in implementation is based on the Netscape Certificate Type extension. You can use this policy to limit the applications for a certificate. In other words, the extension identifies the type of certificate; for example, it identifies whether the certificate is a CA certificate, server SSL certificate, client SSL certificate, object signing certificate, or S/MIME certificate.
This extension has no default value.
If enabled, the policy adds the Netscape certificate type extension to all certificates it issues, unless the predicate expression specifies otherwise. The bits set in the extension are formed from the following HTTP input variables:
The input variables are embedded as hidden values in the default enrollment forms--the directory-based, directory- and PIN-based, and manual enrollment forms. For details about these forms, see "Forms for Certificate Enrollment".
Figure 15.11 shows the default directory-based enrollment form for end users with the information related to the Netscape certificate type extension variables highlighted--it shows two of the total number of variables listed above, ssl_client and email, indicating that these bits be set in certificates requested using this form.
Figure 15.11 Netscape certificate type extension-specific variables in enrollment forms
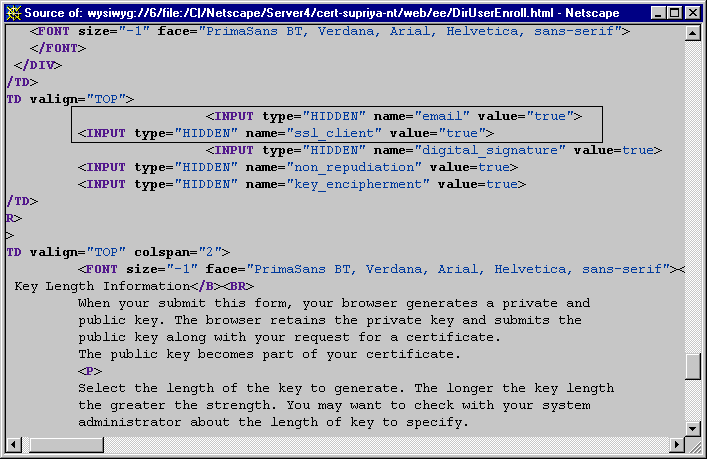
Note that the default enrollment forms embed variables that are considered appropriate for the type of certificate, such as client, server, or CA, that can be requested using the form. For example, the server enrollment form embeds the ssl_server variable, whereas the subordinate CA (Certificate Manager) enrollment form embeds the ssl_client, email_ca, ssl_ca and object_signing_ca variables.
In general, the forms are set up so that you don't have to make any modifications. However, if there is a need to modify make sure that the HTML input format is as follows:
<input type="HIDDEN" value="true" name="variable_name">
where variable_name can be any of the variables listed above.
For general guidelines on setting Netscape certificate type extension, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Plug-in for Netscape Certificate Type Extension Policy
The plug-in module provided for the Netscape certificate type extension policy is identified as follows:
com.netscape.certsrv.policy.NSCertTypeExt
Configurable Parameters
Figure 15.12 shows how the configurable parameters pertaining to the NSCertTypeExt policy plug-in implementation are displayed in the CMS window.
Figure 15.12 Parameters and values for the NSCertTypeExt module
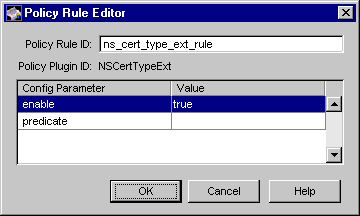
The configuration shown in Figure 15.12 enforces a rule that the Netscape certificate type extension must be set in all certificates.
Table 15.15 gives details about each of these parameters.
Subject Alternate Name Extension Policy
The SubjectAltNameExt policy plug-in implementation is based on the Subject Alternate Name extension. If enabled, this policy checks the certificate request for a mail attribute, and if it is present, adds the subject alternate name extension to the certificate being issued. Both the built-in directory-based authentication modules can obtain a mail attribute from the authentication directory and set that attribute in the certificate request. For more information on the mail attribute, see the description for the ldapAttributes parameter in Table 9.1 and Table 9.2.
For general guidelines on setting the subject alternate name extension, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Plug-in for Subject Alternate Name Extension Policy
The plug-in provided for the subject alternate name extension policy is identified as follows:
com.netscape.certsrv.policy.SubjectAltNameExt
Configurable Parameters
Table 15.16 provides details for the configurable parameters pertaining to the SubjectAltNameExt policy plug-in implementation.
Subject Key Identifier Extension Policy
The SubjectKeyIDExt policy plug-in implementation is based on the Subject Key Identifier extension. This extension provides a means of identifying certificates that contain a particular public key. In other words, this extension is used to uniquely identify a certificate from among several that have the same subject name.
The key identifier set in the extension is the MD5 hash of the subject's public key information.
If enabled, this policy adds the subject key identifier extension to all certificates being issued, unless the predicate specifies otherwise. To facilitate chain building, this extension must appear in all conforming subordinate CA certificates (subordinate Certificate Managers' CA signing certificates).
Therefore, the predicate expression is set to certType==ca by default--so that the extension is added to only subordinate CA certificates. However, you may modify the predicate expression to add this extension to other or all certificates.
If added to end-entity certificates, the subject key identifier extension provides a means for identifying certificates containing the particular public key used in an application. If an end entity has multiple certificates, especially from multiple CAs, the subject key identifier provides a means to quickly identify the set of certificates containing a particular public key. If you want to assist applications in identifying the appropriate end-entity certificate, you should modify the predicate expression to add this extension to all end-entity certificates.
For general guidelines on setting the subject key identifier extension, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Plug-in for Subject Key Identifier Extension Policy
The plug-in provided for the subject key identifier extension policy is identified as follows:
com.netscape.certsrv.policy.SubjectKeyIdExt
Configurable Parameters
Figure 15.13 shows how the configurable parameters pertaining to the SubjectKeyIDExt policy plug-in implementation are displayed in the CMS window.
Figure 15.13 SubjectKeyIDExt plug-in module: configurable parameters
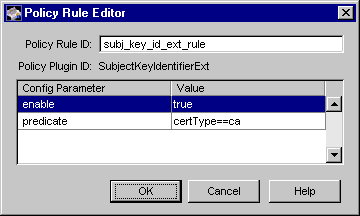
The configuration shown in Figure 15.13 enforces a rule that the subject key identifier extension must be set in all CA certificates.
Table 15.17 provides details for each of these parameters.