For purposes of the following discussions, security refers to the process of encrypting data before it is transmitted over a network. A server running in secure connection mode means that encryption is turned on for all incoming connections. Of course there are other security risks besides someone trying to break your encryption. Along with encryption, you can take other steps to add security to your server. See "Increasing server security" for more information about these steps.
 his chapter describes some of the concepts behind authenticated and encrypted server communications.
Authentication verifies the identity of the client or server.
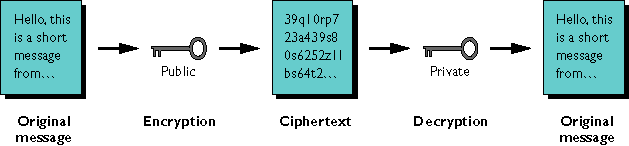
Encryption ensures that data cannot be deciphered if it is intercepted during transmission or if it is received by the wrong parties.
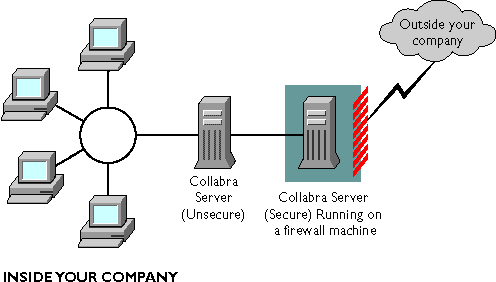
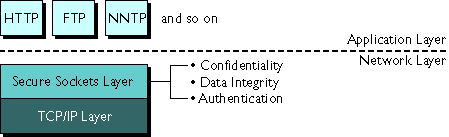
The Netscape Collabra Server uses an advanced protocol called Secure Sockets Layer (SSL) for transferring private data over TCP/IP networks. SSL ensures privacy when communicating with other SSL-enabled products, such as Netscape Navigator, Netscape Communicator, and other SSL-enabled news servers.
This chapter provides a general overview of SSL, authentication, and encryption. More details can be found in the administration server documentation, Managing Netscape Servers.
If you are already familiar with SSL, authentication, and encryption, and you only want to know how to enable SSL for your server, you can skip the overview material. See "Enabling SSL on your server" instead.
his chapter describes some of the concepts behind authenticated and encrypted server communications.
Authentication verifies the identity of the client or server.
Encryption ensures that data cannot be deciphered if it is intercepted during transmission or if it is received by the wrong parties.
The Netscape Collabra Server uses an advanced protocol called Secure Sockets Layer (SSL) for transferring private data over TCP/IP networks. SSL ensures privacy when communicating with other SSL-enabled products, such as Netscape Navigator, Netscape Communicator, and other SSL-enabled news servers.
This chapter provides a general overview of SSL, authentication, and encryption. More details can be found in the administration server documentation, Managing Netscape Servers.
If you are already familiar with SSL, authentication, and encryption, and you only want to know how to enable SSL for your server, you can skip the overview material. See "Enabling SSL on your server" instead.