|
Chapter 1
Introduction to Certificate
Management System
This chapter introduces Netscape Certificate Management System (CMS), a highly configurable set of software components and tools for creating, deploying, and managing certificates.
The chapter has the following sections:
This guide assumes that you are familiar with the concepts of public-key cryptography and digital certificates. For a list of key concepts and information on where to learn more about them, see What You Should Already Know.
|
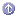 System Overview System Overview |
|
Netscape Certificate Management System provides a highly scalable, easily deployable certificate infrastructure for supporting encryption, authentication, tamper detection, and digital signatures in networked communications. It is based on open standards and protocols that include the following:
Certificate Management System leverages Netscape Directory Server and Netscape Console to provide a complete, scalable, high-performance certificate management solution for extranets and intranets. Its strong support for existing and evolving standards makes Certificate Management System especially well-suited for large heterogeneous extranets that must support a variety of platforms, client and server software, hardware devices such as routers and hardware tokens, virtual private network (VPN) implementations, existing intranet security systems, and so on. It can been customized and configured to fit widely varying deployment scenarios, permitting rapid integration with existing client and server software, customer databases, security systems, and authentication procedures.
This chapter describes the basic features and capabilities of Certificate Management System. Chapter 2, "Default Demo Installation," describes how to install a simple demo that uses some of these features.
Public-Key Infrastructure
The standards and services that facilitate the use of public-key cryptography and X.509 version 3 certificates in a networked environment are collectively called public-key infrastructure (PKI). In any PKI, a certificate authority (CA) is a trusted entity that issues, renews, and revokes certificates. An end entity (EE) is a person, router, server, or other entity that uses a certificate to identify itself.
To participate in a PKI, an end entity must enroll, or register, in the system. The end entity typically initiates enrollment by giving the CA some form of identification and a newly generated public key. The CA uses the information provided to authenticate, or confirm, the identity. In some cases the CA may require human intervention, such as an interview or examination of notarized documents, to authenticate the end entity (manual approval). In other cases the information provided may be sufficient (automatic approval). In addition to authenticating the end entity, the CA uses the public key to ensure "proof of possession"--that is, cryptographic evidence that the certificate request was signed by the holder of the corresponding private key. Finally, the CA issues a certificate that associates the end entity's identity with the public key, and signs the certificate with the CA's own private signing key.
Netscape Certificate Management System dramatically simplifies the PKI enrollment process. Before you deploy a PKI, however, you need to make many decisions about the relationships between CAs and end entities and related policies and procedures.
End entities and CAs may be in different geographic or organizational areas or in completely different organizations that are linked through an extranet (that is, the extension of a company's internal network, or intranet) to selected customers, suppliers, and mobile employees via the Internet. CAs may include third parties that provide services through the Internet as well as the root CAs and subordinate CAs for individual organizations. Policies and certificate content may vary from one organization to another. For all these reasons and many others, the deployment and long-term management of any large-scale PKI require careful advance planning and custom configuration.
Subsystems of Certificate Management System
To meet the widest possible range of configuration requirements, Certificate Management System permits the independent installation of three separate subsystems, or "managers," that typically play distinct roles:
The Certificate Manager, Registration Manager, and Data Recovery Manager subsystems are all highly customizable and can be installed in a variety of configurations and physical locations. Decisions about the number of subsystems to install, where to install them, and the relationships among them and one or more public directories affect all aspects of installation and configuration. Some organizations may want to install a single Certificate Manager on one machine inside the firewall and a single Registration Manager on a separate machine outside the firewall. Others may have a single CA run by a single Certificate Manager and hundreds of Registration Managers in different geographic locations. Still others may have many different CAs or subordinate CAs, and only a few Registration Managers. For descriptions of some basic deployment options, see Chapter 3, "Planning Your Deployment."
Basic System Configuration
Figure 1.1 illustrates some of the data formats and protocols used among the three independent CMS managers and various kinds of end entities. To keep things simple, the figure assumes that each manager is installed in a different CMS instance and on a different machine. The Registration Manager handles all interactions with different kinds of end entities, using protocols appropriate for each entity.
Figure 1.1 Basic CMS configuration and use of data formats and protocols 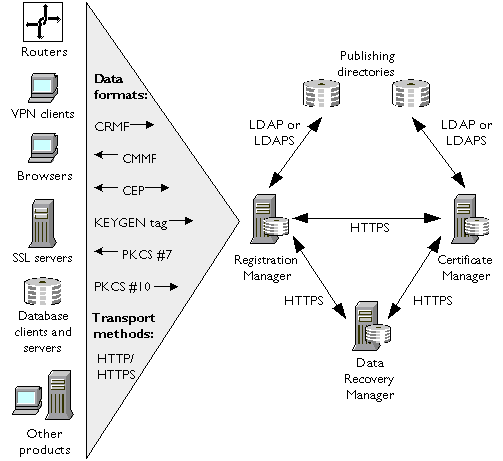
The end-entity data formats and transport methods shown in the figure are used to send enrollment and other requests to the Registration Manager (indicated by a right-pointing arrow) or to send responses back to the end entities (indicated by a left-pointing arrow). The end-entity data formats can be summarized as follows:
These are the standard transport methods used for all of the data formats described above:
For more information about end-entity data formats and protocols used by Certificate Management System, see End Entities and Life-Cycle Management and Standards Summary.
The Registration Manager communicates with the Data Recovery Manager and the Certificate Manager as necessary to facilitate certificate management operations such as enrollment, renewal, or key storage. When the three subsystems are installed in separate CMS instances (whether on the same machine or on different machines), they communicate with each other over HTTPS--that is, HTTP over SSL, as shown in Figure 1.1.
The Certificate Manager can publish certificates and CRLs to a public directory using LDAP or LDAP over SSL (LDAPS). It's also possible for the Registration Manager to publish certificates. However, the Certificate Manager has the complete record of issued certificates, so it is recommended that publishing tasks be performed by the Certificate Manager only. If it's necessary for some entries in a directory to be available outside the firewall, Netscape recommends using the partial replication feature of Directory Server to replicate the relevant portion of the directory to which the Certificate Manager publishes. In this guide, a directory used for publishing certificates and CRLs is called a publishing directory. Publishing directories can also be used for authentication.
Each CMS manager has its own internal LDAP directory for storing private information such as certificate records, key archival records, and the request queue. For example, the Certificate Manager uses its directory for storing certificates and certificate requests; the Registration Manager uses its directory for storing certificate requests (but not certificates, which are stored by the Certificate Manager only); and the Data Recovery Manager uses its directory for storing archived encryption keys. These internal directories are configured during installation. They allow Certificate Management System to leverage the scalability and industry-leading performance of Netscape Directory Server, which replaces the Relational Database Management System (RDBMS) used in Certificate Server 1.x.
Some deployments require installation of two subsystems in a single CMS instance on a single machine: either Certificate Manager and Data Recovery Manager or Registration Manager and Data Recovery Manager. For these dual-manager installations, communication between the two subsystems takes place internally (that is, within the same running process) rather than via HTTPS. (Note that a Certificate Manager performs all Registration Manager tasks, including end-entity interactions. Registration Managers are required only for remote or delegated administration of the CA.)
Throughout this guide, the term CMS administrator describes the person who installs and configures one or more managers and sets up privileges for the users who manage those subsystems. The users who manage day-to-day interactions of end entities with each manager, as well as other aspects of the PKI, are called CMS agents collectively, or the Certificate Manager agent, Registration Manager agent, and Data Recovery Manager agent. The role of an agent is to approve, defer, or reject requests using Agent Services web pages served by the CMS manager for which that agent has been assigned the necessary privileges. The privileges of each agent can be confined to a specific manager or can include several different managers.
System administrators set up CMS subsystems through Netscape Console, and agents manage end-entity requests and certificates through HTML pages. For more information about facilities available to administrators and agents, see Chapter 2, "Default Demo Installation."
|
 Authentication and Policy Modules Authentication and Policy Modules |
|
Certificate Management System includes a plug-in architecture for code modules that authenticate user identities and code modules that enforce policies.
Each type of request from an end user--for certificate enrollment, renewal, revocation, or retrieval--is handled by a different servlet, a piece of Java code designed for that kind of request. Each servlet processes the request using the appropriate protocols (such as the KEYGEN HTML tag or PKCS #10) for each type of end entity. Additional servlets control interactions with administrators and agents.
Authentication Modules
An authentication module is a set of rules (implemented as a Java class) for authenticating an end user, server, or other entity that needs to interact with a CMS manager. (Similar rules are used to authenticate agents and administrators, but they are built into Certificate Management System instead of being implemented as plug-in modules.) With a typical end-user enrollment, the user supplies the information requested by the Registration Manager on an enrollment form, and then the servlet uses an authentication module specified within the form to validate the information and authenticate the user's identity. This simple input value makes it possible to use custom authentication for any form without changing the corresponding servlet code.
CMS managers always support client SSL certificate-based authentication (for both agents and end entities) and user-ID-based and password-based authentication for administrators. Registration Managers and Certificate Managers can also be configured to use standard CMS authentication modules that perform directory-based authentication and directory-based personal identification number (PIN) authentication for end entities. Software development kits (SDKs) are available that demonstrate how to write custom authentication modules, for example to authenticate end entities using existing customer databases or security systems.
Policy Modules
After a Registration Manager or Certificate Manager has successfully authenticated an end entity, the entity's request is passed to a policy processor, which sequentially applies a set of policy rules configured for that CMS manager. A policy module is a rule (implemented as a Java class) that validates the contents of a certificate request for that rule and can add or modify any part of a certificate's contents, including validity dates, name constraints, and extensions.
Here are three typical examples of the use of policies:
Steps in End-Entity Enrollment
The following steps take place when a Registration Manager or a Certificate Manager handles an enrollment request from an end user. Figure 1.2 shows a simplified view of how this works.
Submit form. When the user first interacts with the CMS manager (either the Registration Manager or the Certificate Manager), the user specifies the kind of request to be made, fills in the form for that request, and submits it to the servlet via HTTP or HTTPS. The servlet then processes the form. In the figure, a certificate request is being sent to an enrollment servlet. It could also be a renewal or revocation request being sent to one of the other servlets.
Authenticate user. Authentication can be either automatic or manual. If the CMS manager is configured for automatic authentication, the servlet uses the authentication module specified by the form to validate the information provided by the user. For example, the directory authentication module that comes with Certificate Management System validates the user ID and password by comparing it to the user's entry in an LDAP directory. Custom authentication modules can be used to take advantage of existing databases, security systems, or other methods of authentication. If the CMS manager is configured for manual authentication, the servlet routes the request to the request queue and informs the user (via a web page) that approval has been deferred. The request remains in the queue until an agent approves it or rejects it.
Process policies. If authentication is successful, policies specified for this CMS manager are applied to the request for the purpose of formulating the contents of the certificate to be issued and to enforce certain rules, such as name constraints. Custom policy modules can be used to enforce specialized certificate extensions and other requirements.
Service request. After policy processing, the servlet's work is finished and the CMS manager services the request (assuming that a policy has not triggered deferral)--for example, by issuing a certificate.
Notify user. If the CMS manager has been configured for automatic authentication and issuance, the manager delivers the signed certificate to the user via a web page. If the request has been deferred (for example, for manual approval) or rejected, the user is informed of the request's status. When the request has been approved and the certificate issued, the CMS manager notifies the user (for example, with an email) and provides a URL where the certificate can be picked up.
Since all three CMS managers use the same architecture for authentication and policy processing, it's possible to reuse any authentication and policy modules with any manager. For information on the relationship of policy modules to the APIs exposed by Certificate Management System, see System Architecture.
Figure 1.2 Roles of servlets, authentication modules, and policy modules in end-entity
enrollment 
|
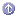 Some Enrollment Scenarios Some Enrollment Scenarios |
|
Successful PKI deployment requires flexible and easy enrollment for end entities as well as ongoing support for certificate life-cycle management--that is, management of each certificate from enrollment through encryption key storage (if necessary), renewal, and revocation. The preceding section describes the internal flow of control among servlets, authentication modules, and policy modules in a CMS manager (see Figure 1.2 for a summary). The examples that follow illustrate the flexibility that the CMS architecture supports among end entities, Registration Managers, Certificate Managers, and existing customer databases, security systems, and directories.
For the sake of simplicity, these examples do not show the role of the Data Recovery Manager. For more information about data recovery, see Data Recovery Manager.
For more information about certificate life-cycle management, see End Entities and Life-Cycle Management.
Firewall Considerations
Most of the examples that follow show a Certificate Manager inside the firewall and a Registration Manager outside the firewall. Other variations are possible, but this arrangement is often appropriate. These are some of the advantages:
Administrative and physical arrangements are closely related to firewall issues. The flexibility of CMS deployment options makes it possible to divide functions among existing administrative groups or physical locations, requiring minimal disruption for an organization.
The examples that follow do not address the role of the Data Recovery Manager or the potential use of multiple Registration Managers and Certificate Managers. For example, in some circumstances it might make sense to have some Registration Managers outside the firewall and some inside; in other cases different CMS subsystems might be located in entirely different physical locations, each with their own firewalls.
In general, Netscape recommends that the Certificate Manager handle all certificate and CRL publishing functions. If it's necessary for some entries in a directory to be available outside the firewall, Netscape recommends using the partial replication feature of Directory Server to replicate the relevant portion of the directory.
Extranet/E-Commerce: Acme Sales Corp.
Acme Sales is a high-end mail-order catalog service that is launching an online shopping service. Many of Acme's affluent customers make very expensive purchases, so Acme has decided to use certificate-based authentication for its new web site.
Acme has 100,000 existing customers and expects to attract many new customers through its online service. The company wants to use its existing relational database to authenticate and enroll existing customers with minimal effort on their part. For new customers, Acme wants to establish a manual process entailing out-of-band credit checks (that is, checks that don't involve an electronic network), identity verification, and a personal phone call before an online certificate request can be granted. In addition, Acme plans to issue certificates to contract workers, suppliers, and employees who routinely access parts of the company's internal network by using Kerberos.
The sections that follow describe how Acme uses Certificate Management System to achieve these goals:
In all cases, Acme has decided to place its Certificate Manager behind the firewall and its Registration Manager outside the firewall, for reasons summarized in Firewall Considerations .
Enrolling Existing Customers
Acme has decided on the following process for registering its existing customers, as shown in Figure 1.3.
Request certificate. The customer fills in and submits a form (over SSL) that specifies account information and other personal details stored in the existing customer database.
Custom authentication. The Registration Manager uses a custom authentication module to verify the customer's account and status against the existing customer database.
Request certificate. If authentication against the customer database is successful, the Registration Manager performs policy processing and, if processing is successful, forwards the request to the Certificate Manager.
Issue certificate. The Certificate Manager performs its own policy processing and, if processing is successful, issues the certificate and delivers it to the Registration Manager.
Deliver certificate. If the Certificate Manager successfully issues the certificate, the Registration Manager delivers it to the end user in the same session. If the request is unsuccessful for any reason, the Registration Manager displays a web page to the customer explaining the problem and what to do about it.
Figure 1.3 Custom authentication against an existing customer database 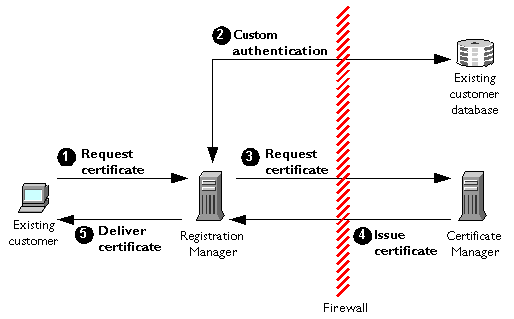
Enrolling New Customers
The following process will be used for enrolling new Acme customers. In this case, the Registration Manager uses manual authentication to validate every certificate request personally before issuing the certificate. Figure 1.4 illustrates the steps in this process.
Request certificate. The customer fills in and submits a certificate request form for new Acme customers.
Deferral notice. The Registration Manager immediately informs the customer (via a web page) that the request has been deferred and that Acme will be in touch soon. Meanwhile, the certificate request waits in a queue for attention from the Registration Manager agent.
Manual approval. The Registration Manager administrator may configure the Registration Manager to notify the agent via email whenever a new request is added to the request queue. In any case, when the agent processes the requests in the queue, he or she follows Acme's procedure for processing credit checks and validating other customer information, including making a personal phone call. If all authentication procedures are successful, the agent approves the request.
Request certificate. The Registration Manager performs policy processing and, if the processing is successful, sends the approved request to the Certificate Manager.
Issue certificate. The Certificate Manager performs its own policy processing on the request and, if processing is successful, issues the certificate and delivers it to the Registration Manager.
Email notice of issuance. The Registration Manager sends an email containing a URL to the new customer, asking the customer to pick up the certificate.
Pick up certificate. The customer goes to the specified Registration Manager URL and picks up the certificate.
Figure 1.4 Manual authentication of new customers 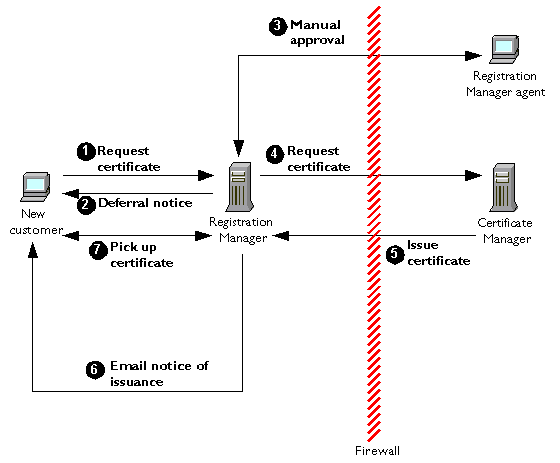
Enrolling Extranet Users
Acme wants its new, certificate-enabled extranet applications to be available to contract workers, suppliers, employees, and others who routinely access parts of the company's internal network. In general, this can be achieved by using Kerberos or other non-PKI security systems as the authentication mechanism for requesting a certificate. To authenticate them for the purposes of PKI enrollment, Acme uses a third-party authentication module from DASCOM that takes advantage of its existing Kerberos system without disturbing its current functions.
For example, to get a certificate, a contractor provides an ID and password to the Registration Manager, which uses the Kerberos system to verify them before passing on the certificate request to the Certificate Manager. This arrangement involves the following steps, illustrated in Figure 1.5. (The details of the existing security system don't matter: third-party or custom CMS authentication modules can be used for Kerberos, NIS, and many other security systems. Extranet users can continue to use applications based on the old security systems while they use their certificates to take advantage of new certificate-based applications.)
Request certificate. A user of Acme's existing extranet fills in and submits a certificate request (over SSL) using a customized form that requires a Kerberos ID and password.
Authentication. The Registration Manager uses a third-party authentication module to validate the user's identity using the existing internal Kerberos system.
Request certificate. If authentication against Kerberos is successful, the Registration Manager performs policy processing and, if processing is successful, forwards the request to the Certificate Manager.
Issue certificate. The Certificate Manager performs its own policy processing on the request and, if processing is successful, issues the certificate and delivers it to the Registration Manager.
Deliver certificate. If the Certificate Manager issues the certificate, the Registration Manager delivers it to the end user in the same session. If the request is unsuccessful for any reason, the Registration Manager displays a web page to the user explaining the problem and what to do about it.
Figure 1.5 Custom authentication against an existing Kerberos security system 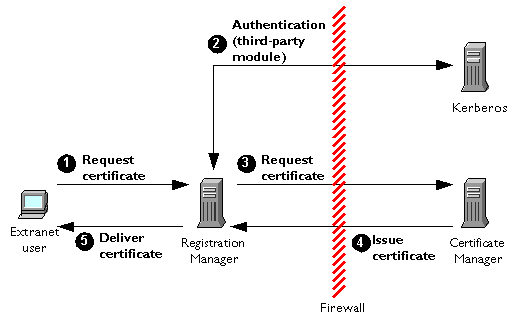
PIN Registration: Atlas Manufacturing
Atlas Manufacturing has decided to put information for its employees, suppliers, dealers, and customers--a total of nearly 500,000 people, including individual consumers and employees of several dozen other companies--on an extranet. Atlas already uses Netscape Directory Server to store names, addresses, and other information about the various groups of people who will need access to the extranet. To register all these people at once, Atlas uses the directory-based PIN Generator tool that comes with Certificate Management System to generate PINs in bulk. The PINs are then stored in the directory and delivered to the end users via a batch mailer program, an employee payroll stub, a customer invoice, or some other means of physical delivery.
PINs are salted and hashed before storage in the directory. Salting refers to the inclusion of additional information from the distinguished name (DN) with the PIN to ensure unique hashing. Hashing, in this case, involves generating a number of fixed length from the PIN and DN information. Even if the security of the directory is breached, it is very difficult to reconstruct the PIN from the value that results from salting and hashing. When customers use the PIN to enroll in the Atlas PKI, the PIN is automatically removed from the directory. Enrollment PINs are therefore more reliable than passwords, which must be protected over a long period of time.
Acme's process involves the following steps (illustrated in Figure 1.6):
Generate PINs. The CMS administrator runs the CMS PIN Generator against the existing directory, populating each entry with a unique PIN.
Write out PIN records. The CMS administrator uses the CMS PIN Generator to write out PIN records for use by an out-of-band delivery mechanism.
Out-of-band delivery. The user receives the PIN via a batch mailing system, payroll stub, invoice form, or other out-of-band delivery mechanism.
Request certificate (using PIN). The user goes to a specified Registration Manager URL, fills in name and PIN, and submits a certificate request.
Authentication (using PIN). The Registration Manager uses the standard CMS PIN-based directory authentication module to verify the PIN against the directory.
Request certificate. If authentication against the directory is successful, the Registration Manager performs policy processing and, if this succeeds, forwards the request to the Certificate Manager.
Issue certificate. The Certificate Manager performs its own policy processing and, if all goes well, issues the certificate.
Deliver certificate. If the Certificate Manager issues the certificate, the Registration Manager delivers it to the end user in the same session. If the request is unsuccessful for any reason, the Registration Manager displays a web page to the user explaining the problem and what to do about it.
Figure 1.6 PIN-based enrollment 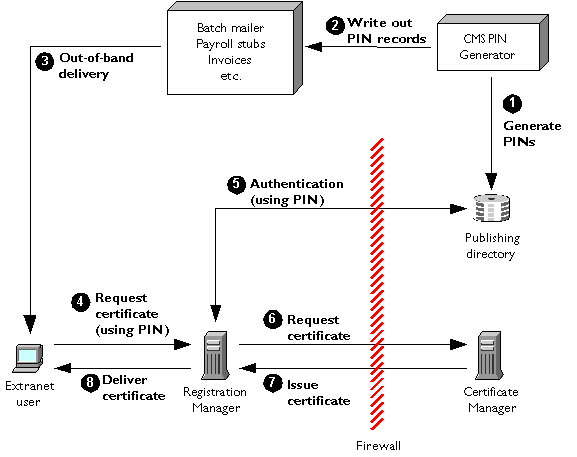
VPN Client Enrollment and Revocation
Virtual private network (VPN) client software runs on a user's desktop, outside the firewall, and uses the IP Key Management Protocol (IPKMP) or IP Security (IPSec) protocol to establish encrypted communication with VPN hardware that straddles the firewall. These protocols allow VPN hardware to authenticate VPN client software using the client's certificate, in much the same way that the SSL protocol allows a server to authenticate client browser software.
VPN client software can use several different protocols over HTTP or HTTPS to handle enrollment and other life-cycle management tasks. Certificate Management System supports the Certificate Enrollment Protocol (CEP) used by Cisco routers. CEP runs over HTTP and provides its own form of encryption.
The following steps explain how VPN client software can use the Registration Manager and Certificate Manager to enroll in a PKI and what happens when the client's certificate is revoked. These steps are shown in Figure 1.7.
Enroll in PKI. The VPN client sends a certificate request to the Registration Manager via CEP, and the Registration Manager processes the request and forwards it to the Certificate Manager inside the firewall. (Any of the authentication methods discussed in the previous sections can be used during enrollment to authenticate the client.)
Issue certificate. The Certificate Manager issues the certificate, and the Registration Manager delivers it to the VPN client. The VPN client can now authenticate itself to the VPN hardware and establish an encrypted channel using IPKMP or IPSec. All TCP/IP communication passes through this encrypted channel. From the point of view of the VPN client, it appears to be directly connected to the TCP/IP network inside the firewall.
Publish certificate. The Certificate Manager publishes the certificate to a directory (this is an optional step).
Revoke certificate. After some time has passed, the Certificate Manager agent revokes the certificate (for example, after the certificate owner leaves the company).
Publish CRL. The Certificate Manager publishes a new CRL to the directory specified as the CRL distribution point in the original certificate.
Verify certificate. The VPN hardware checks the CRL as part of its authentication process. Certificates listed in the CRL are not authenticated, and VPN clients presenting them cannot establish a connection.
Figure 1.7 VPN client enrollment and revocation 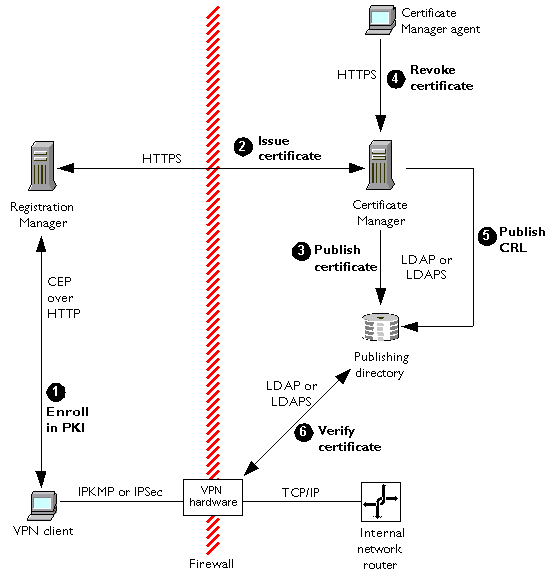
The certificate includes information about a CRL distribution point, which is a directory that the VPN hardware can check for the latest CRL published by the Certificate Manager.
Router Enrollment and Revocation
Cisco routers support the use of certificates for authentication, encryption, and tamper detection with the IP Security (IPSec) protocol. Cisco routers also support CEP for certificate life-cycle management, as discussed in the previous section.
The following steps describe how two routers can use a Certificate Manager to enroll in a PKI and what happens when a router's certificate is revoked. These steps are shown in Figure 1.8.
Enroll in PKI. The routers each send a certificate request to the Certificate Manager via CEP, and the Certificate Manager issues them certificates. (Any of the authentication methods discussed in the previous section can be used during enrollment to authenticate the client.)
Publish certificates. As part of the issuing process, the Certificate Manager publishes the certificates to the directory. (Publishing occurs only if the router's DN exists in the publishing directory. This is important for some Cisco routers that must fetch their certificates from an LDAP directory because flash memory is not large enough to hold them.) The routers can now authenticate each other and establish an encrypted channel using IPSec. All TCP/IP communication passes through this encrypted channel. From the point of view of other connections to each router, they all appear to be sharing the same TCP/IP network.
Revoke a certificate. After some time has passed, the Certificate Manager agent revokes one of the certificates (for example, after the certificate owner leaves the company).
Publish CRL. The Certificate Manager publishes the CRL to the directory.
Verify certificate. The routers check the CRL as part of their mutual authentication process. Certificates listed in the CRL are not authenticated, and routers presenting them cannot establish a connection.
Figure 1.8 Router enrollment and revocation 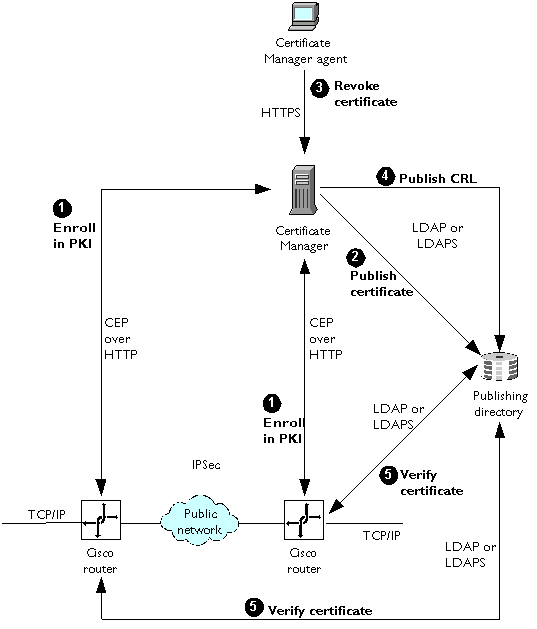
|
 End Entities and Life-Cycle Management End Entities and Life-Cycle Management |
|
Certificate Management System provides default web forms for all end-entity interactions involved in managing the life cycle of a certificate. It also provides forms, collectively called Agent Services, for agent interactions. These forms can be used as is or customized. The sections that follow introduce the end-entity forms and protocols.
Life-Cycle Management Formats and Protocols
The Registration Manager and Certificate Manager provide default HTML forms that use different protocols and life-cycle management procedures for different kinds of end entities. For example, end entities running Navigator 3.x and versions of Communicator earlier than 4.5 need to be presented with an enrollment form based on the use of the HTML tag KEYGEN to generate keys. End entities running Microsoft Internet Explorer require a form containing VBScript XENROLL commands. These various tags, scripts, and protocols result in enrollment messages that are sent back to the Certificate Manger or Registration Manager in a variety of nonstandard and standards-based formats.
Table 1.1 summarizes the message formats, cryptographic algorithms, and key pairs (single or dual) supported by Certificate Management System for the main categories of end-entity software. Note that, for the purposes of enrollment, CMS managers are also end entities. CMS managers installed in different instances need SSL client and SSL server certificates to identify themselves. For more information about the standards listed in Table 1.1, see Standards Summary.
Access to Subsystems
Three kinds of entities can access CMS subsystems: administrators, agents, and end entities. Administrators are responsible for the initial setup and ongoing maintenance of the subsystems. Agents manage the day-to-day operations of each subsystem, such as responding to requests from end entities. End entities access Registration Manager or Certificate Manager subsystems to enroll in a PKI and to take part in other life-cycle management operations, such as renewal or revocation.
Figure 1.9 shows the ports used by administrators, agents, and end entities. All agent and administrator interactions with CMS subsystems occur over HTTPS. For detailed information on the use of the Agent Services interface by agents and the use of Netscape Console by administrators, see Netscape Certificate Management System Agent's Guide and Netscape Certificate Management System Administrator's Guide, respectively.
End-entity interactions can take place over HTTP or HTTPS. For example, routers using CEP, which includes its own encryption scheme, uses HTTP rather than HTTPS. For a more detailed discussion of these ports and examples of hands-on use, see Chapter 2, "Default Demo Installation."
Figure 1.9 Access ports for Certificate Management System 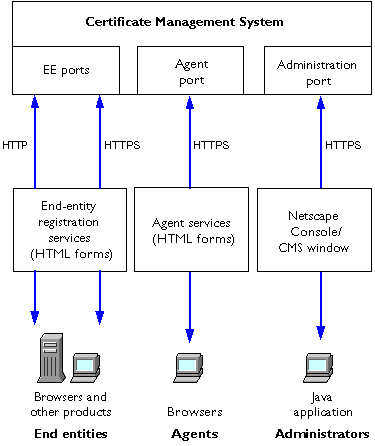
HTML Forms for End Users
Each type of end-entity form provided by a Registration Manager or Certificate Manager determines the type of client, such as Communicator or Internet Explorer, and presents the appropriate input page. Each form also specifies both an authentication module and an output template. The authentication module is used by the servlet to authenticate the end entity; the output template is an HTML page that returns information from the servlet to the end entity.
Figure 1.10 shows the default manual enrollment form as it is presented to end users running Communicator 4.5. Users can click items in the left menu and tabs to access other HTML forms. Server administrators, including CMS administrators, can also access forms for enrolling servers or subsystems. Any of these forms can be customized to reflect an organization's requirements.
Figure 1.10 Default manual enrollment form for end users 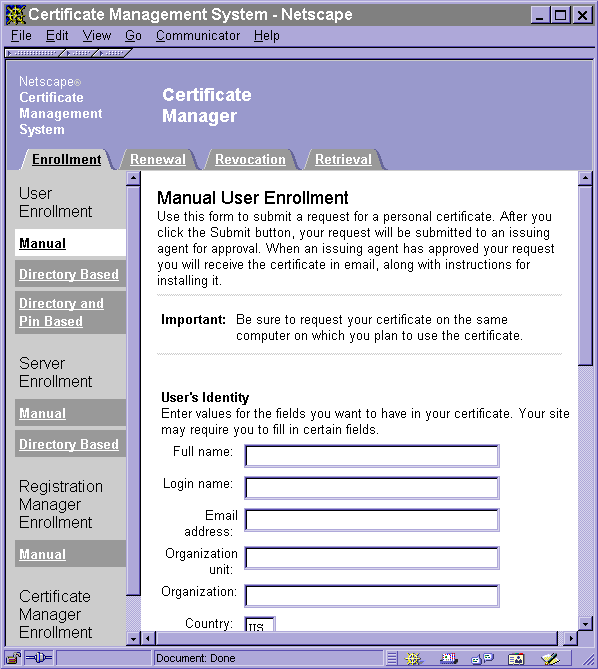
Table 1.2 shows the protocols supported by the default CMS life-cycle management servlets. Any of the HTML forms and their HTML help text can be customized. The Registration Manager also supports the creation of new forms. Some output templates can also be customized.
For more information about the standards listed in Table 1.1, see Standards Summary.
|
 Summary of System Features Summary of System Features |
|
This section summarizes the most important out-of-the-box features that Netscape Certificate Management System offers in the following areas:
For detailed descriptions of the agent interfaces used to control these features in CMS subsystems, see Netscape Certificate Management System Agent's Guide.
Authentication Modules
An authentication module is a set of rules (implemented as a Java class) for authenticating an end entity, agent, administrator, or any other entity that needs to interact with a CMS manager. For an introduction to the role of authentication modules in the enrollment process, see Authentication and Policy Modules.
All CMS managers support client SSL certificate-based authentication (for both agents and end entities). Netscape Console supports user ID- and password-based authentication for administrators. Registration Managers and Certificate Managers also support three authentication modules out of the box:
When you configure either of the directory-based authentication modules, you can specify how the DN should be used to formulate the subject name. As a result, neither the user nor the agent needs to figure out or enter the subject name--its formulation is entirely automated.
It's also possible to write custom authentication modules, for example to authenticate end entities by using existing customer databases or security systems. For example, DASCOM Inc. provides a DCE Kerberos authentication module.
Sample code provided with Certificate Management System demonstrates how to write custom authentication modules. The most recent version of CMS code samples can be found at http://home.netscape.com/eng/server/cms/.
For information about ways customized authentication modules can be used during enrollment, see Some Enrollment Scenarios.
Policy Modules
A policy module is a rule (implemented as a Java class) that validates the contents of a certificate request and formulates the contents of the certificate to be issued. Policy modules are also responsible for accepting, rejecting, or deferring the request. Certificate Management System policies have nothing to do with export control policies or certificate usage policies. For an introduction to the role of policy modules in the enrollment process, see Authentication and Policy Modules.
Certificate Management System supports the following constraints-specific policy modules out of the box. These policies establish rules or constraints that Certificate Management System must use to evaluate an incoming request. They can be used with either a Certificate Manager or a Registration Manager.
Certificate Management System supports the following policy modules out of the box for formulating certificate extensions. They can be used with either a Certificate Manager or a Registration Manager.
In addition to the modules listed above, sample code provided with Certificate Management System demonstrates how to support several additional extensions, including Name Constraints, Policy Constraints, and Extended Key Usage. The most recent version of CMS code samples can be found at http://home.netscape.com/eng/server/cms/.
For detailed information about using certificate extensions, see Appendix B, "Certificate Extensions."
Job Scheduler Plug-Ins
The CMS Job Scheduler allows you to configure a Certificate Management System to perform a specified action at a specified time, such as informing a user of the need to renew a certificate or removing an expired certificate from the directory. The scheduler checks at specified intervals for jobs waiting to be executed; if the specified execution time has arrived, the scheduler initiates the job.
You can use standard CMS job plug-ins or write your own Java plug-in class in much the same way that you can write your own authentication and policy modules. Plug-in classes are provided out of the box for scheduling the following jobs:
Event-Driven Notifications
The Certificate Manager and Registration Manager support two kinds of event-driven notifications:
Registration Manager
A Registration Manager is a trusted subsystem to which a Certificate Manager can delegate responsibility. A Registration Manager cannot issue or revoke certificates by itself; instead, it evaluates end-entity requests and forwards them to a Certificate Manager for action, such as the issuing of a certificate.
A Registration Manager is designed to handle certificate life-cycle management tasks--that is, the tasks required to maintain a certificate throughout its life cycle, including the following:
A Registration Manager's default forms for end-entity interactions can be used as is or customized. For more information about default Registration Manager forms, see End Entities and Life-Cycle Management.
Certificate Manager
A Certificate Manager can be configured to accept requests from end entities, from Registration Managers, or from both end entities and Registration Managers. When set up to work with a remote Registration Manager, the Certificate Manager processes requests and returns the signed certificates to the Registration Manager, which distributes them to end entities.
Basic capabilities of the Certificate Manager (as distinct from the Registration Manager) include the following:
Although it is possible to configure a Registration Manager to publish certificates to an LDAP directory, the Certificate Manager maintains a complete record of issued certificates, so it is recommended that publishing tasks be performed by the Certificate Manager only.
The Certificate Manager can issue certificates with the following characteristics:
Signing Algorithms
The Certificate Manager supports the following signing algorithms for both certificates and CRLs:
Certificate Revocation Lists
The Certificate Manager can issue X.509 v1 or v2 CRLs. A CRL can be automatically updated whenever a certificate is revoked or at specified intervals.
CRL extensions supported include the following:
The following CRL extensions are not supported:
CRL entry extensions supported include the following:
The CRL entry extension Hold Instruction Code is not supported.
Data Recovery Manager
A Data Recovery Manager provides facilities for archiving and recovering private RSA encryption keys. This crucial element of a PKI allows an authorized Data Recovery Manager agent to recover an encryption key that has been lost or corrupted. It also allows administrators to recover encryption keys for employees who have left the company or who are unavailable for some other reason. In either case, once the encryption key has been recovered, the user or administrator can use it to decrypt any data (such as saved email messages) that was encrypted with that key.
A Data Recovery Manager can be used with dual key pairs only--that is, with end entities that support a signing key pair and signing certificate and an encryption key pair and encryption certificate for each identity, and that also support archival of encryption keys. Dual key pairs allow an end entity to get a new signing certificate and signing key pair without changing the encryption certificate or encryption key pair. Similarly, an end entity or an administrator can recover a lost encryption key without changing the signing certificate or signing key pair.
The Data Recovery Manager uses two special key pairs in the process of archiving an end entity's encryption key: a transport key pair (and certificate) and a storage key pair. The end entity must also have two key pairs: a signing key pair and an encryption key pair. The roles of all these keys are summarized in Table 1.3.
The following steps summarize the key storage process during end-entity enrollment through a Registration Manager. Figure 1.11 illustrates these steps.
After the user completes and submits an enrollment form, the end entity generates dual key pairs and sends two certificate requests to the Registration Manager, which detects a request for key archival and requests the private encryption key from the end entity. The end entity then encrypts (or "wraps") its newly minted private encryption key with the Data Recovery Manager's public transport key (obtained from a copy of the transport certificate embedded in the enrollment form) and sends the wrapped private key to the Registration Manager.
The Registration Manager sends the end entity's wrapped private encryption key to the Data Recovery Manager as part of a key storage request (which also includes the end entity's public encryption key).
The Data Recovery Manager uses its private transport key to decrypt the end entity's private encryption key. After confirming that the private encryption key corresponds to the end entity's public encryption key, the Data Recovery Manager encrypts the private encryption key with its private storage key and stores the private encryption key in the CMS internal database.
The Data Recovery Manager signs a proof-of-archival token with its private transport key and sends the token to the Registration Manager.
The Registration Manager verifies the token and sends the certificate requests on to the Certificate Manager.
The Certificate Manager issues the signing and encryption certificates and sends them back to the Registration Manager
The Registration Manager delivers the certificates to the end entity.
Figure 1.11 Key storage process during end-entity enrollment 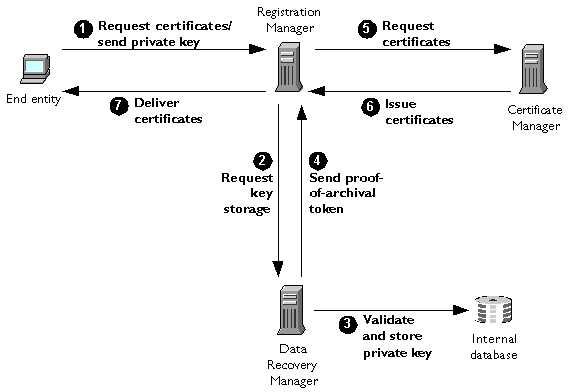
Data encrypted with the storage key can be retrieved only if m of n "split keys" are provided at the same time by m of n authorized recovery agents. By default, m and n are 2 and 3, respectively. Both values can be changed, as long as m is less than or equal to n.
The Data Recovery Manager indexes stored keys by owner name and a hash of the public key. This arrangement allows for highly efficient searching by name (all stored keys belonging to that owner are returned) or by public key (only the requested key is returned).
Command-Line Utilities
Table 1.4 summarizes the command-line utilities that are bundled with Certificate Management System. For more detailed information about these utilities, see Appendix D and the appendixes that follow in Netscape Certificate Management System Administrator's Guide. The binaries for the tools listed in the table are located in the directory <serverroot>/bin/cert/tools.
The first five tools listed in Table 1.4 (AtoB, BtoA, PrettyPrintCert, PrettyPrintCrl, and dumpasn1) are useful for converting back and forth between various encodings and formats you may encounter when dealing with keys and certificates.
The Certificate Database Tool, Key Database Tool, and Security Module Database Tool (which is described in Appendix B of Managing Servers with Netscape Console) are useful for a variety of administrative tasks that involve manipulating certificate and key databases.
The Migration Tool converts Certificate Server 1.x data for use with Certificate Management System, and the PIN Generator tool creates PINs for directory authentication.
The Netscape Signing Tool associates a digital signature with any file. For information about using this tool to sign CMS logs, see "Signing Log Files" in Chapter 27 of Netscape Certificate Management System Administrator's Guide.
The SSL Strength Tool and SSL Debugging Tool are useful for testing and debugging purposes.
|
 System Architecture System Architecture |
|
Figure 1.12 shows the internal architecture of Netscape Certificate Management System. The sections that follow describe the basic elements of this architecture, starting at the bottom of the figure.
Figure 1.12 CMS architecture 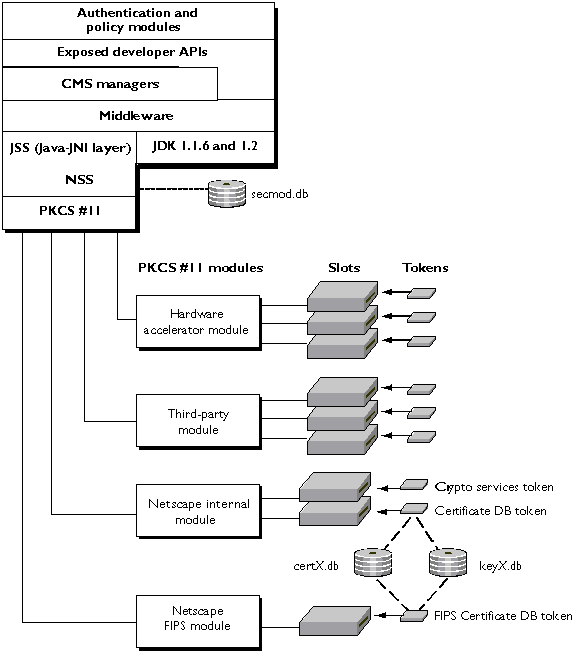
PKCS #11
Public-Key Cryptography Standard (PKCS) #11 specifies an API used to communicate with devices that hold cryptographic information and perform cryptographic operations. Because it supports PKCS #11, Certificate Management System works with a wide range of hardware and software devices intended for such purposes.
One or more PKCS #11 modules must be available to any CMS subsystem instance. As shown in Figure 1.12, a PKCS #11 module (also called a cryptographic module or cryptographic service provider) manages cryptographic services such as encryption and decryption via the PKCS #11 interface. PKCS #11 modules can be thought of as drivers for cryptographic devices that can be implemented in either hardware or software. Netscape provides a built-in PKCS #11 module with Certificate Management System.
A PKCS #11 module always has one or more slots, which can be implemented as physical hardware slots in some form of physical reader (for example, for smart cards) or as conceptual slots in software. Each slot for a PKCS #11 module can in turn contain a token, which is the hardware or software device that actually provides cryptographic services and optionally stores certificates and keys.
Netscape provides two built-in modules with Certificate Management System:
Any PKCS #11 module can be used with Certificate Management System. The server uses a file called secmod.db to keep track of the modules that are available. You can modify this file with the Security Module Database Tool (for details, see Appendix B, "Administration Server Command Line Tools," in Managing Servers with Netscape Console). For example, you need to modify secmod.db if you are installing hardware accelerators for use in signing operations.
NSS
Netscape Security Services (NSS) is a set of libraries designed to support cross-platform development of security-enabled communications applications. Applications built with the NSS libraries support the SSL protocol for authentication, tamper detection, and encryption as well as the PKCS #11 interface for cryptographic token interfaces. Netscape uses NSS to support these features in a wide range of products, including Certificate Management System.
As shown in Figure 1.12, NSS communicates with PKCS #11 modules through the PKCS #11 interface and in turn provides the foundation for Java Security Services and higher Java layers.
JSS and the Java/JNI Layer
Java Security Services (JSS) provides a Java interface for security operations performed by NSS. JSS and higher levels of the Certificate Management System architecture are built with the Java Native Interface (JNI), which provides binary compatibility across different versions of the Java Virtual Machine (JVM). This design allows customized subsystem services to be compiled and built just once and run on a range of platforms.
Middleware/JDK 1.1.6 Layers
A middleware layer above JSS and the Java/JNI layer provides a range of services required by the Registration Manager, Certificate Manager, and Data Recovery Manager. The middleware layer is based on Java Development Kit (JDK) 1.1.6, and it underlies both the manager subsystems and the APIs available to third-party developers for building custom authentication and policy modules. The default authentication and policy modules provided with Certificate Management System are built from the same Java classes.
Authentication and Policy Modules
The top layer of Figure 1.12 consists of authentication and policy modules. Several default modules ship with Certificate Management System; third parties can create their own custom modules using the APIs provided above the middleware and subsystem layers. Modules for all three subsystems work the same way and are interchangeable.
|
 Standards Summary Standards Summary |
|
This section summarizes the standard message formats and protocols supported by Certificate Management System.
Certificate Management Formats and Protocols
Certificate Management System supports the following certificate management formats and protocols. For more details about the proposed PKIX standards listed here, see http://www.ietf.org/html.charters/pkix-charter.html (under Internet Drafts).
Security and Directory Protocols
Certificate Management System supports the following security and directory protocols:
|
|
|
|